Security issues remain a key challenge in cloud adoption while the ever increasing need for more software drives cost and complexity up. Unikernels are widely acknowledged as the future of cloud infrastructure yet they remain inaccessible to most organizations.

(Sample Nginx Application Deployed as Nanos Unikernel)
What gives it that security?
Ransomware is terrorizing banks, hospitals, and entire cities. There is a new data breach every single day affecting millions. Nation states and other large scale threat actors are stealing sensitive IP and proprietary data.
Listen, we could lie and say unikernels are un-hackable but you obviously know that's not true. What our goal here is to elevate the conversation and attack known problems that have afflicted servers for a long time.
Single Process
Linux and Windows are both multiple process systems that were designed decades ago and could not envision the cloud environment we live and work in today. Unikernels are single process systems. By design they can *not* run other programs that were not intended to run. This makes your attackers actually work to do nasty things versus running some automated script. Most RCE attacks are predicated on the fact that you can eventually run other programs on that server - without that environment you've immediately made it much more difficult to do anything interesting.
No Users
When your website boots up you not only have remote code execution in place but you have tens of potential users that can login to execute said code (and they are always "bad users"). Unikernels have *no* users and this massively reduces remote code execution - it's designed that way. No more Equifax incidents - not on your watch.
No Shell
The shell is at least a 40 year old construct designed in a different time period. Today in Silicon Valley engineers are used to working with tens, hundreds, thousands or even more systems at a time. It's an antiqutated concept that only lends it's hands towards those who want to do your company harm. There are no shells on unikernel systems - they simply don't exist. They can not exist. This is by design.
Reduced Attack Surface
Compared to a bloated Linux system that has hundrds of millions of lines of code with drivers for everything from USB drives (which you won't use on the cloud) to audio drivers (which you won't use on the cloud) to libraries such as libxslt that have ftp servers embedded in them unikernels are refreshingly small. Sometimes as small as 10Mb or maybe even kilobytes. Smaller than some of the images on this webpage.
Yes, Nanos unikernels have all the same security protections you'd find in a Linux system and more:
ASLR
- Stack Randomization
- Heap Randomization
- Library Randomization
- Executable Randomization
Page Protections
- Stack Execution off by Default
- Heap Execution off by Default
- Null Page is Not Mapped
- Stack Cookies/Canaries
- Rodata no execute
- Text no write
STIG Security Control Reduction
Further, if you are in a regulated sector Nanos unikernels can dramatically reduce the security controls on a given environment. That's time back in your pocket.
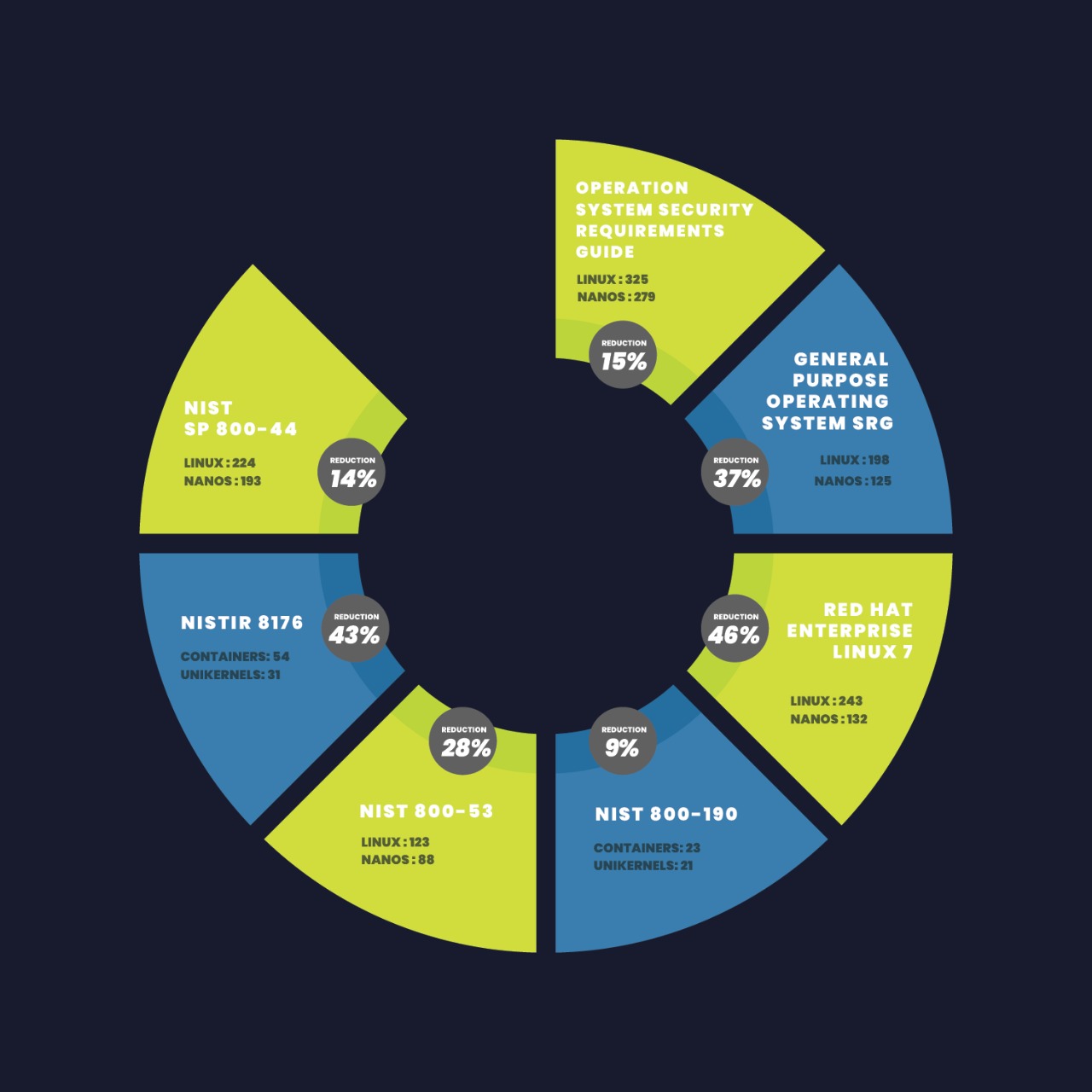
Less code == Less exploits
Introducing the future cloud.